Talk about memory safety at ONE Conference

ONE Conference
ONE Conference is an invite-only, two-day cybersecurity conference held annually at the World Forum in The Hague.
With 1400 attendees this year, 200 speakers, and some 100 sessions spread over 8 different tracks, it was an excellent place to learn a lot and connect with many people. I very much enjoyed the friendly atmosphere, the stories people shared from first-hand experience, and the fact that the sessions ranged from very accessible to very technical.
The keynote was delivered by our prime minister Dick Schoof, who asked for concrete ways of moving forward with security by design. This, of course, is exactly what we were there for.
 Image: Marc and Hugo at ONE Conference 2025
Image: Marc and Hugo at ONE Conference 2025
You’re not secure if you’re not memory safe
Our talk titled ‘You’re not secure by design, if you’re not memory safe’ made the case for memory safety as a cornerstone of applying security by design in practice.
To set the scene, we first drew a historical analogy with the rise in seatbelt use in cars from the 1970s and the resulting rapid decline in fatal car crashes. We posited that an increased use of memory safe technology will similarly result in a decline of critical software vulnerabilities; e.g. the vulnerability that allowed the Chinese to spy on our Ministry of Defense, and the one that allowed hackers to disrupt our public prosecution service for months.
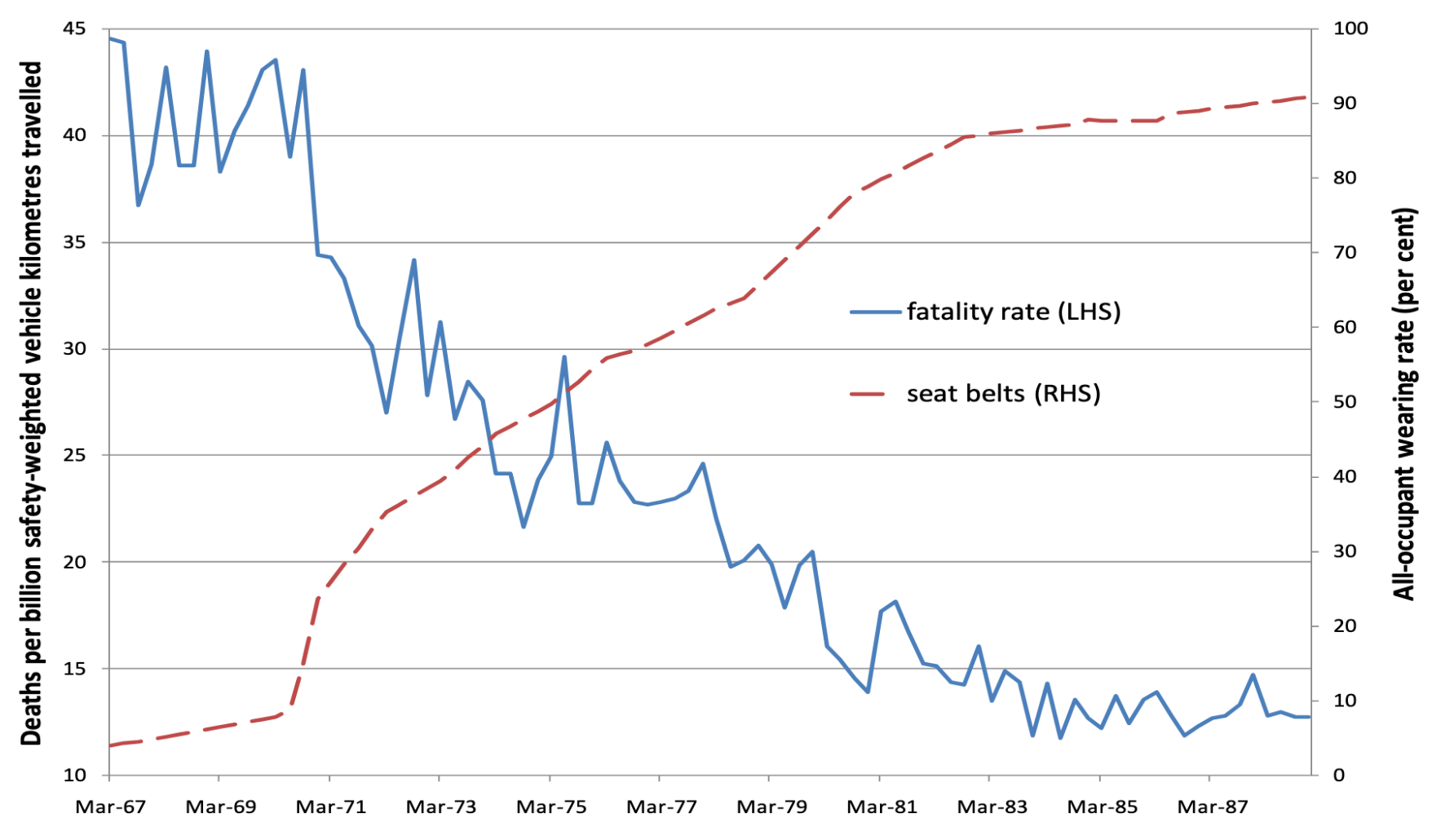 Graph: number of seatbelts worn versus deaths in car accidents
Graph: number of seatbelts worn versus deaths in car accidents
From there, we discussed the importance of security by design in the evolving European legislative context, made the case for memory safety, and gave a brief overview of what has been said about memory safety in CISA’s secure by design campaign.
The slides are available for download here. If you have any questions or feedback, please let us know!
The case for memory safety
If you’re curious about the relevance of memory safety – or why we, a company whose core business is building reliable software with Rust and helping others do the same – decided to spend our time on this talk, here is a crash course answer.
With the rising number of digital threats, the current geopolitical tensions, and the rapidly evolving legislative context in Europe, the need to apply security by design in practice has increased significantly. We feel very strongly that using modern memory safe technology should be seen as foundational for ‘practising’ security by design; After all, up to 70% of security vulnerabilities in legacy memory-unsafe codebases are due to mishandling memory. And these are codebases that nearly all of us use and rely on every day. Eliminating these vulnerabilities is therefore urgent; memory safety should be a no-brainer.
Using modern memory-safe tech like Rust, Go and Swift not only dramatically improves security outcomes for end-users, it also has all sorts of secondary benefits, such as a better developer experience and increased productivity.
What’s next?
Advocating memory safety is an ongoing effort. We look forward to the public commenting phase (enquiry) for the horizontal standards that are being developed for the Cyber Resilience Act; We are curious to see how much concrete language they contain regarding the use of modern memory safe programming languages.
In that same context, we are finalizing an upcoming publication that calls for European policymakers to incentivize the use of memory safe technology. More on this topic soon!