A safe Internet requires secure time

Currently, the safety of the web relies on our devices being properly synchronized, which in turn relies on the Network Time Protocol.
This protocol is generally used completely unprotected, much like the web was before HTTPS; if our devices were to receive a manipulated timestamp, they wouldn’t know. The solution is to facilitate the adoption of Network Time Security (NTS), by developing an open and public pool of NTS servers.
Contents
- Towards a secure web
- When trust expires
- Status quo: Unsecured time
- The unused solution: Network Time Security (NTS)
- The plan for NTS adoption: the NTS Pool
- Funding the secure timing effort
Towards a secure web
In order to understand where we are coming from, we’d like to take you back a little. In 2010, most websites you visited served their content unencrypted over HTTP. HTTP is problematic: all data is sent unencrypted, resulting in issues like hijacking online payments or ISPs manipulating website content. For example, Britain's GCHQ intelligence agency used it to attack Belgian ISPs.
Fortunately, the web has largely transitioned to HTTPS traffic, based on the Transport Layer Security (TLS) protocol, securing traffic from manipulation by third parties and preventing these kinds of attacks. Nowadays you don’t have to worry about anybody manipulating the content of a webpage. And you can safely enter your payment information in a webshop.
For all of this to work, one important aspect is establishing trust. This is not an easy problem to solve as your computer only knows the domain name of the website you’d like to communicate with; that’s it. How can we trust someone we know nothing about?
Browser vendors solved this by allowing a select few organizations to issue certificates proving that a website is owned by the same person who owns the domain name. This is comparable to how governments can issue passports for their citizens, and that passport verifies that this person is who they say they are.
When trust expires
Trust is never absolute. Our passports are only valid for a limited amount of time to limit the usefulness of a stolen passport and to allow new anti-forgery measures to be introduced.
The same is true for website certificates. This validity period is essential in multiple ways: it allows new cryptographic standards while old ones eventually expire. And without a validity period, a certificate would be trusted forever once issued. What if the owner of a domain name changed?
To ensure that trust can expire, a computer must know the current time.
“Time is crucial for an increasingly wide range of internet applications and services. For example, internet security protocols like TLS (secures end-to-end communication), DNSSEC (secures domain name to IP address mappings), and RPKI (secures routes across the internet) cannot function without accurate time, nor can a function such as domain name registration.”
From 'An open infrastructure for sub-millisecond internet time' by Cristian Hesselman, Marco Davids, Giovane Moura
Knowing the current time isn’t just limited to TLS and the web. Authentication protocols like Time-based One-Time Password (TOTP) and Kerberos also require knowledge of the current time and don’t function correctly without it. Chat systems like Signal embed the current time in their messages to validate when they were sent. Not knowing the current time opens your system up to all kinds of attacks and makes it hard or impossible to communicate with the rest of the world.
In essence, your device becomes untrusted - and it doesn’t trust other systems anymore - if it isn’t synchronized with the rest of the world.
Status quo: Unsecured time
Knowing how important properly synchronized time is, you’d expect the distribution of the current time to your device to be a non-issue - a solved problem, no major issues. However, most devices primarily use the Network Time Protocol (NTP) to synchronize their time.
This protocol is generally used completely unprotected, much like the web was before HTTPS.
Anyone can easily intercept an NTP message with the current time and then send an arbitrary ‘fake’ time. Some efforts have been made to add random information to NTP messages to make it a little harder to predict how a valid response would look, but the fact remains that there is no protection against manipulation.
The safety of the web (TLS) depends on an unsecured protocol
Think about it: your computer receives the current time, has no way to validate this, and just adjusts its clock to this received time; and whenever it wants to open a secure connection it checks certificate validity against that time - whether it was a genuine, unintercepted NTP message or ‘fake’ time.
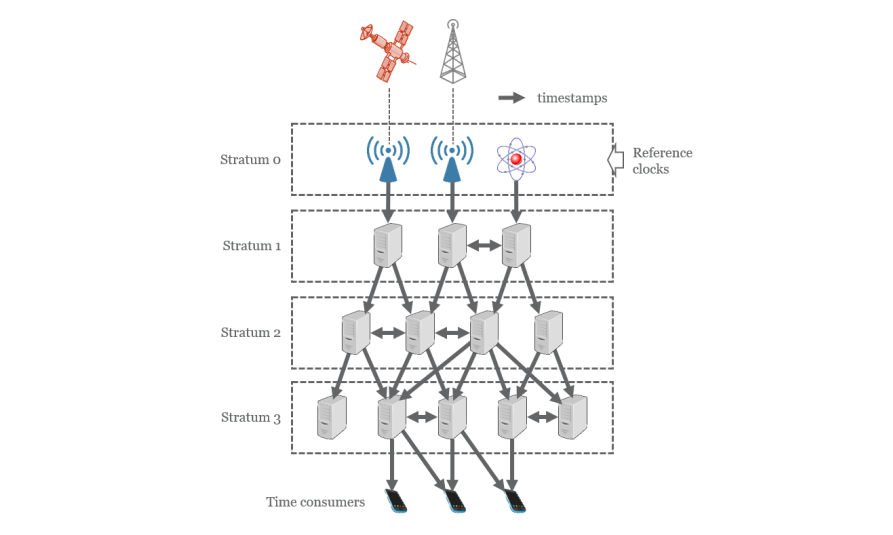
Figure: Organisation of an NTP infrastructure (image created by SIDN Labs), based on Wikipedia)
The unused solution: Network Time Security (NTS)
Fortunately, there is a solution. The Network Time Security (NTS) standard was released in September 2020 to validate that an NTP message was not tampered with. Unfortunately, though, NTS has hardly seen any adoption. Most internet-connected devices still rely on NTP without using NTS to get their time.
This has two causes. First, many client implementations still don’t implement any form of NTS. Second, NTS server availability is limited, and those servers are hard to discover.
These are not insurmountable problems, though. In fact, we have a plan. If we succeed, we will gain a better, more robust, and more secure world.
The plan for NTS adoption: the NTS Pool
Our plan is to develop a public NTS pool that can handle a large set of NTS-capable servers to simplify the discovery of these servers. This includes adding implementations to the major NTS server projects, Chrony, NTPsec, and our own ntpd-rs.
We also aim to massively increase the number of available NTS servers by making it easy to set up and add your own NTS server. This would result in a similar availability as NTP, with its large public pool, pool.ntp.org, being one of the many factors that made NTP so successful.
To show that client NTS support is beneficial for any client we will implement NTS support for the widely used systemd-timesyncd. This SNTP client is used on Linux servers which would especially benefit from securely synchronized time.
Our goal is to show the world that secure time synchronization is within reach and helps to make the internet and our lives more secure.
Read more about the proposed NTS pool in Ruben's blog Enabling pools in NTS.
We believe that important work like this should be public and available to everyone; all our work will be open-source and based on open standards.
Funding the secure timing effort
We need financial backing to start this project. Please get in touch with us via pendulum@trifectatech.org, if you are interested in financially supporting this project.
Why fund us?
Trifecta Tech Foundation, the non-profit backed by Tweede golf, develops and maintains open-source software for vital infrastructure in the public interest. Trifecta Tech Foundation has built modern, open-source implementations of the Network Time Protocol and the Precision Time Protocol, and have submitted a proposal for NTS pools to the IETF.
The team has an in-depth understanding of time synchronization protocols and the development of secure and robust systems software. Working with the timing community and sharing our insights is an integral part of our mission; see trifectatech.org/initiatives/time-synchronization/.
Join Prossimo, Sovereign Tech Fund, SIDN fonds, and NLnet Foundation
Your backing ensures that we can continue to improve the security of time synchronization. You'll join the ranks of Prossimo, Sovereign Tech Fund, SIDN fonds and NLnet Foundation, the world's leading organizations striving for an open and secure internet, who have previously funded our project.
